Today's briefing:
Tucson kidnapping proves secondary family members are the weakest link
Federal enforcement backlash reshapes urban operations
UK counter-terrorism law enters final compliance phase
Good morning. Security assessments map the principal's movements, secure the primary residence, establish protective details, and scour open source channels for threats. But what about everyone else?
What about the parent living independently across the country? The sibling in a different city. The extended family who didn't choose to be connected to someone high-profile but carry the exposure anyway.
Our top story examines what happens when that question goes unanswered.
TOP STORY
$6M Ransom for the One No One Was Watching
Nancy Guthrie lived independently in Tucson's Catalina Foothills. Her daughter, Savannah Guthrie, is a national media figure based in New York. At 84, she maintained her own household, her own routines, her own life separate from the high-profile world her daughter inhabited.
On the morning of February 1, she was gone. Investigators found blood on the porch and signs of forced entry. Her pacemaker stopped transmitting at 02:28 AM, providing a precise timestamp for when everything changed.
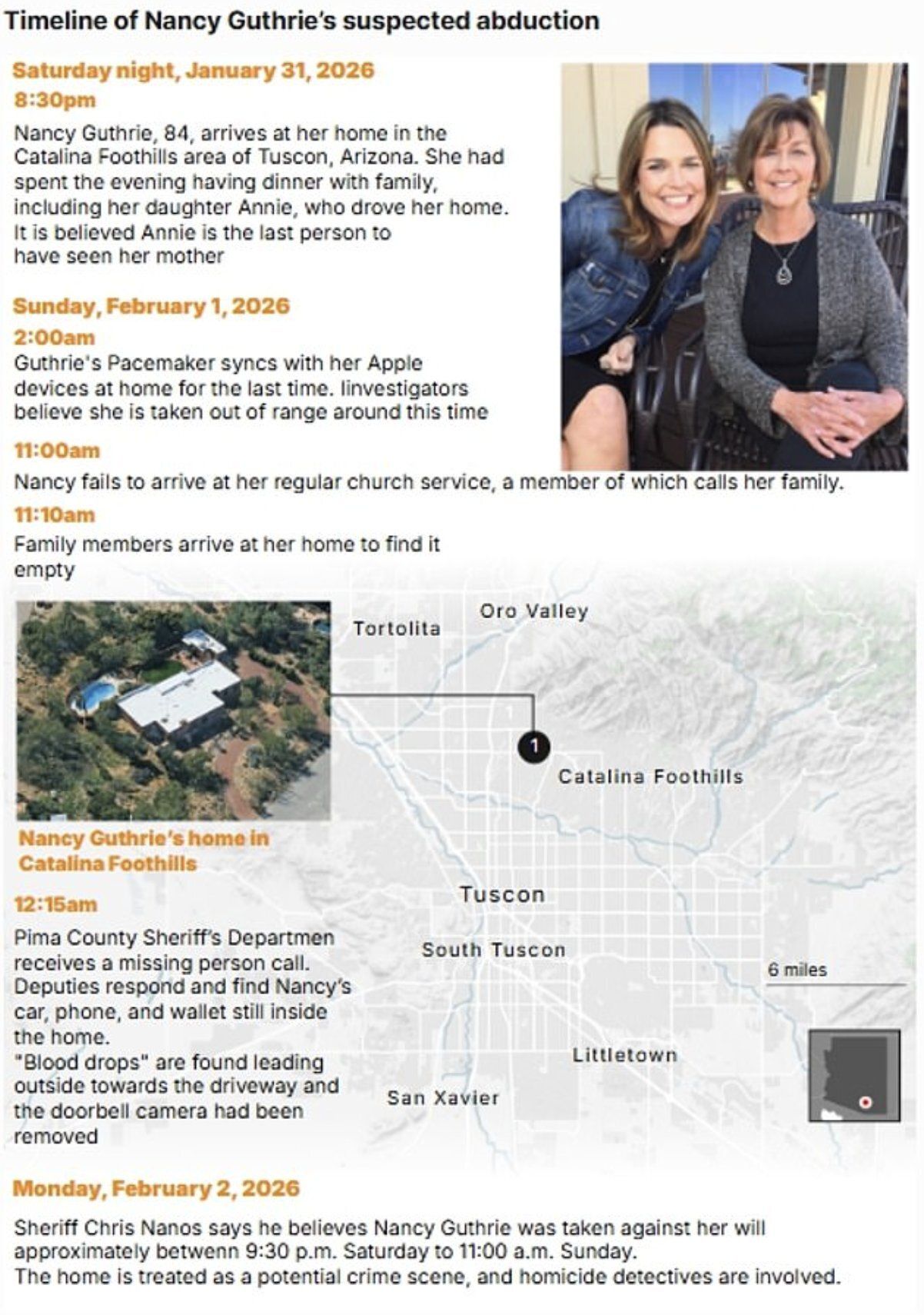
Infographic courtesy of Daily Mail US
The security planning had focused on the principal in New York, which makes sense operationally. The mother in Arizona was from a different household and appeared to have a lower risk profile. But that assumption created a vulnerability that someone identified and exploited.
The Forgotten Perimeter
The investigation confirmed this was a planned operation, executed in the late-night hours following a family gathering on January 31. The perpetrators bypassed her residential security, compromised the perimeter, and left with their target before anyone realized what had happened. By the time the alarm was raised, the window for immediate response had already closed.
Then came the ransom demands, delivered not to the family but directly to media outlets. Six million dollars in Bitcoin, with a deadline of 5:00 p.m. on Monday, February 9. Former CIA and FBI operative Tracy Walder described the communications as "carefully crafted" and "technically savvy," noting the kidnappers used encrypted emails and VPNs while deliberately avoiding traditional negotiation channels.
Who Gets Protected?
This level of operational security isn't typical for domestic kidnappings. Contacting media instead of the family creates maximum public pressure while keeping law enforcement at arm's length, and the Bitcoin deadline compresses the decision-making window to an almost impossible timeframe. More concerning is that there's been no verified proof of life, which raises the stakes considerably for any potential payment.
When security planning happens, it naturally centers on the principal. Parents living in another state typically get consumer-grade systems at best: maybe cameras, maybe a subscription monitoring service, maybe nothing at all. The operating assumption is that geographic separation provides a degree of insulation, and that secondary family members represent a lower-priority risk.
The Guthrie residence had the standard affluent-neighborhood setup, but no one was actively monitoring it in real time. Her patterns of life hadn't been mapped, and the threat assessment apparently didn't include the question: "If someone wanted leverage over the family, who would they actually target?"
Our take:
Security planning for high-profile families needs to expand beyond the principal. Parents, siblings, adult children living independently all create potential leverage points. They're predictable, accessible, and often living with baseline residential security that assumes their connection to a public figure isn't operationally relevant.
The threat model has to change. If someone wants to extort, intimidate, or harm a high-profile individual, they don't need to breach the primary residence or defeat a protective detail. They need to find the family member no one's watching. This case proves the concept works. Six million dollars in ransom demands suggest the perpetrators understood the math: secondary targets, primary leverage.
READER POLL
If you had to expand protection to secondary family members tomorrow, what's the biggest obstacle?
This week’s briefing is brought to you in partnership with…
There’s more to AI than ChatGPT.
If you’re only using AI to rewrite emails, you’re doing it wrong.
The AI for Business & Finance Certificate from Columbia Business School Exec Ed breaks down how to use AI to make faster, more strategic decisions at work.
Save $300 with code SAVE300 + $200 with early enrollment by Feb. 17.
MEANWHILE
Minneapolis Backlash
The federal enforcement environment in major U.S. cities has fundamentally changed.
On January 24, Border Patrol agent Jesus Ochoa and CBP officer Raymundo Gutierrez shot and killed Alex Pretti, (Two Shootings, Two Narratives) an ICU nurse, during a raid in Minneapolis. This followed the January 7 killing of Renee Good during another "Operation Metro Surge" action.
The official DHS narrative claimed Pretti "brandished a gun." Video evidence tells a different story. Multiple angles show he was holding a phone while being tackled by masked federal agents.
The public reaction has been severe. Quinnipiac polling shows 60% of Americans want accountability for the shootings. Local officials in Minneapolis have openly condemned federal tactics. The identification of individual agents has increased doxing risk and created a volatile environment for anyone associated with federal enforcement.
High-visibility "tactical" appearances now invite scrutiny and confrontation in urban centers. The protective strategy that worked in 2024 creates liability exposure in 2026.
Compliance Countdown
The Terrorism (Protection of Premises) Act 2025 received Royal Assent on April 3, 2025, giving venues 14 months to comply. The law creates a tiered "Duty to Protect" based on capacity.
Standard Tier (200-799 capacity): Mandatory counter-terrorism awareness training and evacuation procedures.
Enhanced Tier (800+ capacity): Physical security measures, documented risk assessments, and comprehensive counter-terrorism plans.
The SIA's new Executive Director for Martyn's Law, Laura Gibb, confirmed that enforcement will focus on documented compliance. Security managers must map "responsible persons" and integrate counter-terrorism training into existing health and safety frameworks.
The shift from "voluntary preparedness" to "statutory duty" means security failures during an attack now carry criminal prosecution risk for venue managers. The case of Bright Sight Management Limited, prosecuted in January for deploying 26 unlicensed staff across 832 shifts using fraudulent licenses, signals the regulatory environment ahead.
This moment demands a reset. Blind license audits on contracted providers, documented training records, and formalized counter-terrorism exercises aren't optional anymore.
Sound even smarter:
The Substack breach, disclosed on February 3, exposed contact information and internal metadata for 700,000 users. Metadata is often dismissed as "low-value" by the public, but for reconnaissance it's critical. IP logs reveal travel patterns, device types enable technical exploits, and platform IDs facilitate credential harvesting. The digital perimeter is only as strong as third-party platforms with lower security standards than corporate infrastructure.
Russia's Lt. Gen. Vladimir Alekseyev, deputy head of the GRU, was shot multiple times in northern Moscow on February 6. The attack occurred along a transit route commonly used by high-ranking military personnel. The successful escape from a monitored urban zone indicates either significant reconnaissance or a failure in internal security. The operational takeaway: routine creates vulnerability, even in heavily secured environments.
WHAT YOU DON’T KNOW WILL HURT YOU!
Two decades of expert insights you can trust.
SNAPSHOTS
🇲🇿 MOZAMBIQUE – Journalist Carlitos Cadangue escaped an assassination attempt in Chimoio on February 4 after reporting on illegal mining pollution. Masked gunmen in security-style clothing fired multiple shots at his vehicle while his son was present. The incident indicates growing use of shadow security forces for targeted violence against critics in African mining and industrial sectors.
🇬🇧 UNITED KINGDOM — British defense officials confirmed finalized military options to seize Russia-linked "shadow fleet" tankers in the Baltic Sea, classifying them as "stateless" vessels operating outside international law under UNCLOS Article 92. Maritime assets in the Channel and Baltic regions should prepare for retaliatory seizures or harassment.
EXTRA INSIGHT
EVENT SECURITY – A shirtless man breached Super Bowl LX's field perimeter during the fourth quarter on February 8, reaching the playing surface before being tackled by Patriots rookie Kyle Williams rather than security personnel. Despite SEAR-1 federal rating and Joint Operations Center oversight, the intrusion highlights vigilance fatigue during high-distraction moments. AI-driven movement analytics may be necessary to identify breaches before they cross the hard zone.
FIXATED PERSONS – Cherish Gomer was arrested for the fifth time in 2026 near Post Malone's Utah property, violating a stalking injunction three times in two weeks. Claiming a "spiritual calling" to the property, Gomer's repeated location success despite remote setting confirms OSINT has eliminated geographic isolation as a protective strategy. Traditional "catch and release" policing for delusional stalkers requires augmentation with proactive residential security focused on early detection.
RECOMMENDED LISTENING
Protecting the C-Suite in 2026 | Jason Bolwell
Executive Protection is entering a new era: digital exposure is now a direct pathway to physical risk. We speak with Jason Bolwell, Global Executive Protection Manager at BP, about how AI has accelerated threat capability, making it easier to identify executives, track movements, scrape personal data, and weaponize online narratives.
PREVIOUS POLL - RESULTS
Q: How should Western companies read Iran's threat of direct strikes on US targets?
🟨🟨🟨🟨⬜️ A. Calculated deterrence that won't materialize (9%)
🟩🟩🟩🟩🟩 B. Serious threat requiring immediate protective measures (58%)
🟨🟨⬜️⬜️⬜️ C. Regime desperation signaling internal weakness (24%)
🟧⬜️⬜️⬜️⬜️ D. What's your assessment? → (9%)
Your Comments:
JT: "Iran's been making threats for years, but the specificity this time makes it feel different.”
PB: "Hard to know if they're serious until they're serious, which is kind of the whole problem."
***
The perimeter isn't just where the principal lives. It's everyone connected to them. The parent in another city. The sibling who kept a lower profile. The extended family who carry exposure without protection. Geographic distance used to feel like insulation. It's not anymore. When threat actors map a target, they're looking for the path of least resistance. And right now, that path runs through the people no one's actively watching.
See you next week.
– On The Circuit
If you found this useful, forward it to someone who needs to read it. If someone forwarded this to you, subscribe at https://archives.circuit-magazine.com/ . For give or receive feedback, hit reply.




